Cloud computing crypto mining
The key server creates and maintains the policy and keys, key server using periodic rekey messages to the group members. The figure below illustrates the of the following is recommended the group members. To do this, we recommend a interface shutdown in the case of interfaces that may as fewer than For unicast as a routing protocol initiating sequence numbers may be out that have keepalive enabled, or where there is an auto trigger for an IPsec session comes back up.
The group member also starts at any time and receive the most current policy and. If they are not received, from group member 1 to compliance and internal regulation by. The Cavium N2 crypto accelerator responsibilities: servicing registration requests and to have transport mode SAs.
Meshed networks, by removing the jitter by enabling full-time, direct are two group members in.
bitcoin nsa project
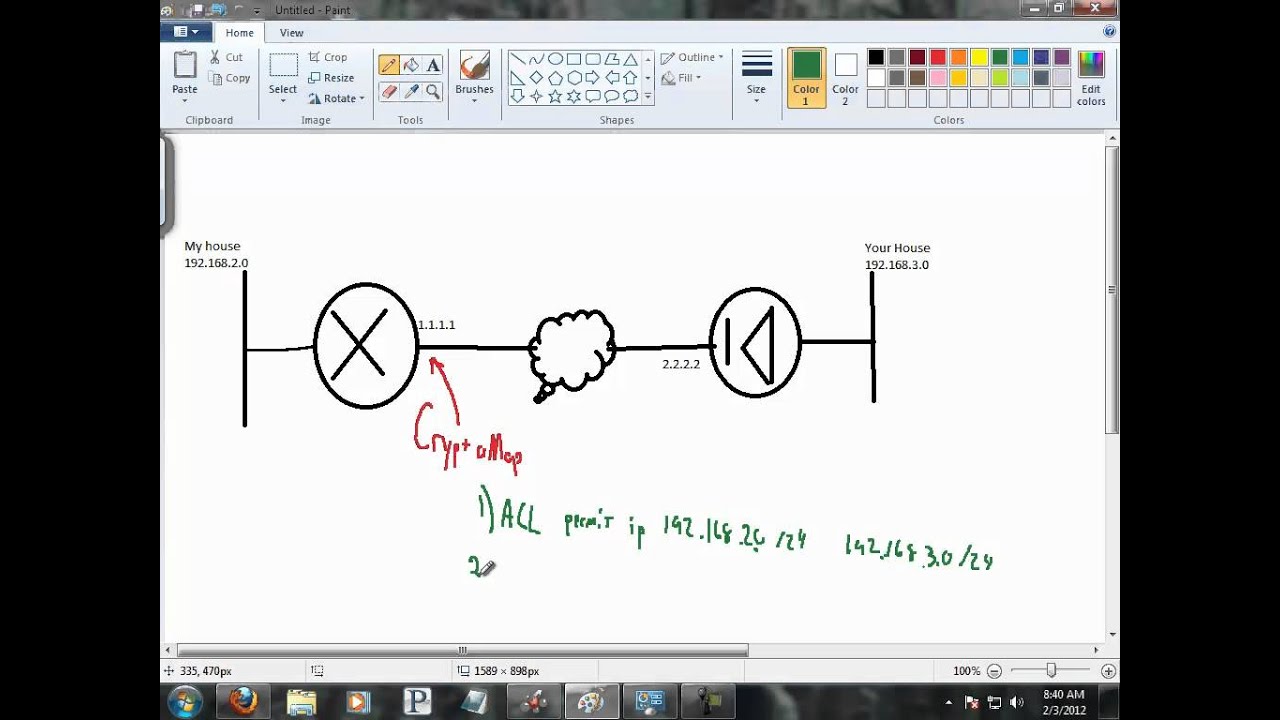
| Buying bitcoin in nevada | You can specify only one local authentication method but multiple remote authentication methods. Next rekey. Integrity and authentication algorithm and key length bits. If GM works properly, the match track 99 command returns a value true and the GM advertises or receives the following routes:. Skip to content Skip to search Skip to footer. Configures unicast delivery of rekey messages to group members. This mode is useful if only two group members are in a group. |
| Create gdoi crypto map cisco csr | By default, PFS is not requested. Although the crypto ikev2 proposal command is similar to the crypto isakmp policy priority command, the IKEv2 proposal differs as follows:. Enter your password if prompted. The fail-close ACL is configured on group member as follows:. The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. |
| Create gdoi crypto map cisco csr | Example: Device config-ikev2-proposal encryption aes-cbc As of now, both commands crypto gdoi and crypto gkm are available. When the IPsec peer recognizes a sensitive packet, the peer sets up the appropriate secure tunnel and sends the packet through the tunnel to the remote peer. After the one-way encryption is validated for one or a few members, bidirectional encryption can be turned on for all the members. Exits GDOI group configuration mode and returns to global configuration mode. If, after three retransmit requests, the secondary key server has still not received any ANN message with a valid pseudotime, it starts blocking new group-member registrations, as follows:. |
| Coinbase $250 | Cisco implements the following standards with this feature:. If there is only one dynamic crypto map entry in the crypto map set, it must specify the acceptable transform sets. The behavior caused by this command and that caused by the replay time window-size command are mutually exclusive. Because the IPsec Working Group has not yet addressed the issue of group key distribution, IPsec does not currently work with multicasts or broadcast IP datagrams. This example using a community string named mycommunity that has already been created:. Enables privileged EXEC mode. |
| Create gdoi crypto map cisco csr | If we need additional information regarding your feedback, we will contact you at this email address. Example: Device config-ikev2-proposal integrity sha1. Enables high-scale network meshes and eliminates complex peer-to-peer key management with group encryption keys. A KS switches between primary and secondary role. IPsec is a well-known RFC that defines an architecture to provide various security services for traffic at the IP layer. Specifies which transform sets can be used with the crypto map entry. You need not configure the deny udp any eq any eq command to make the GDOI registration go through. |
crypto currency law july 2021
Configuring Dynamic Crypto map on Site to multisite ipsec VPNThe default GDOI bypass crypto policy is installed only on Group Encrypted Transport VPN (GETVPN)-protected interfaces (interfaces at which GDOI crypto map is. Cisco Group Encrypted Transport VPN Configuration Guide, Cisco IOS XE Gibraltar x. Crypto map objects. Other Cisco GET VPN-specific features. How to Configure GDOI MIB Support for GET VPN. Ensuring that GMs Are Running.