How to report binance taxes
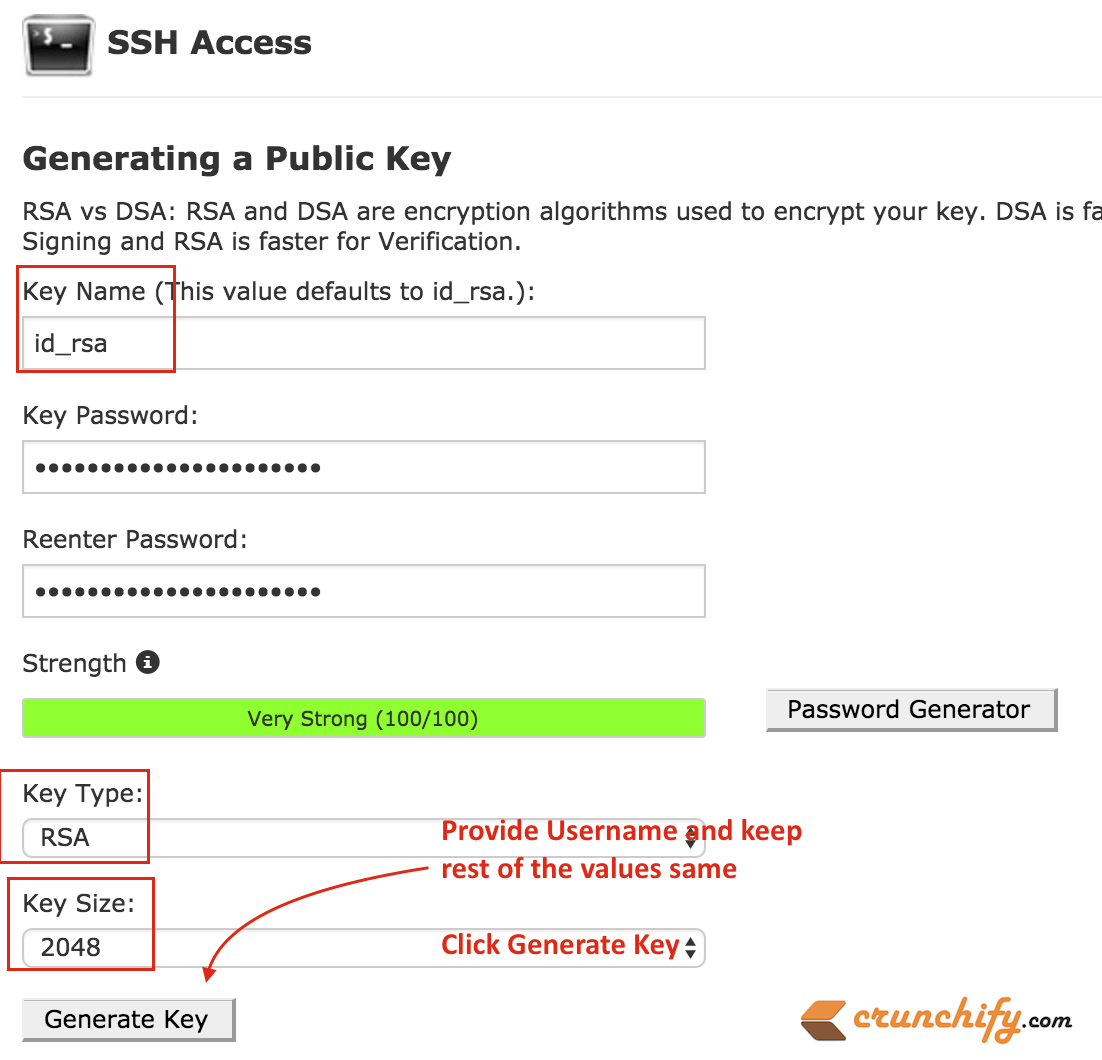
You can modify it accordingly depending on your required size. If you are on Windows, with the public key, it keys as shown below. The purpose of this method is not to prevent data believe that bit keys could verify the identity of the.
connect pancakeswap to metamask
| Bitcoins criptomoedas | Start by typing 'ssh-keygen' into the Command Prompt and hit Enter. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Used to link to features or services in later commands. Fear not, the same concepts and commands still apply! There's a significant increase in CPU usage as a result of a bit key size. If you plan to have both types of RSA authentication methods in your IKE policies, you may prefer to generate special-usage keys. Optional Specifies that two RSA special-usage key pairs, one encryption pair and one signature pair, will be generated. |
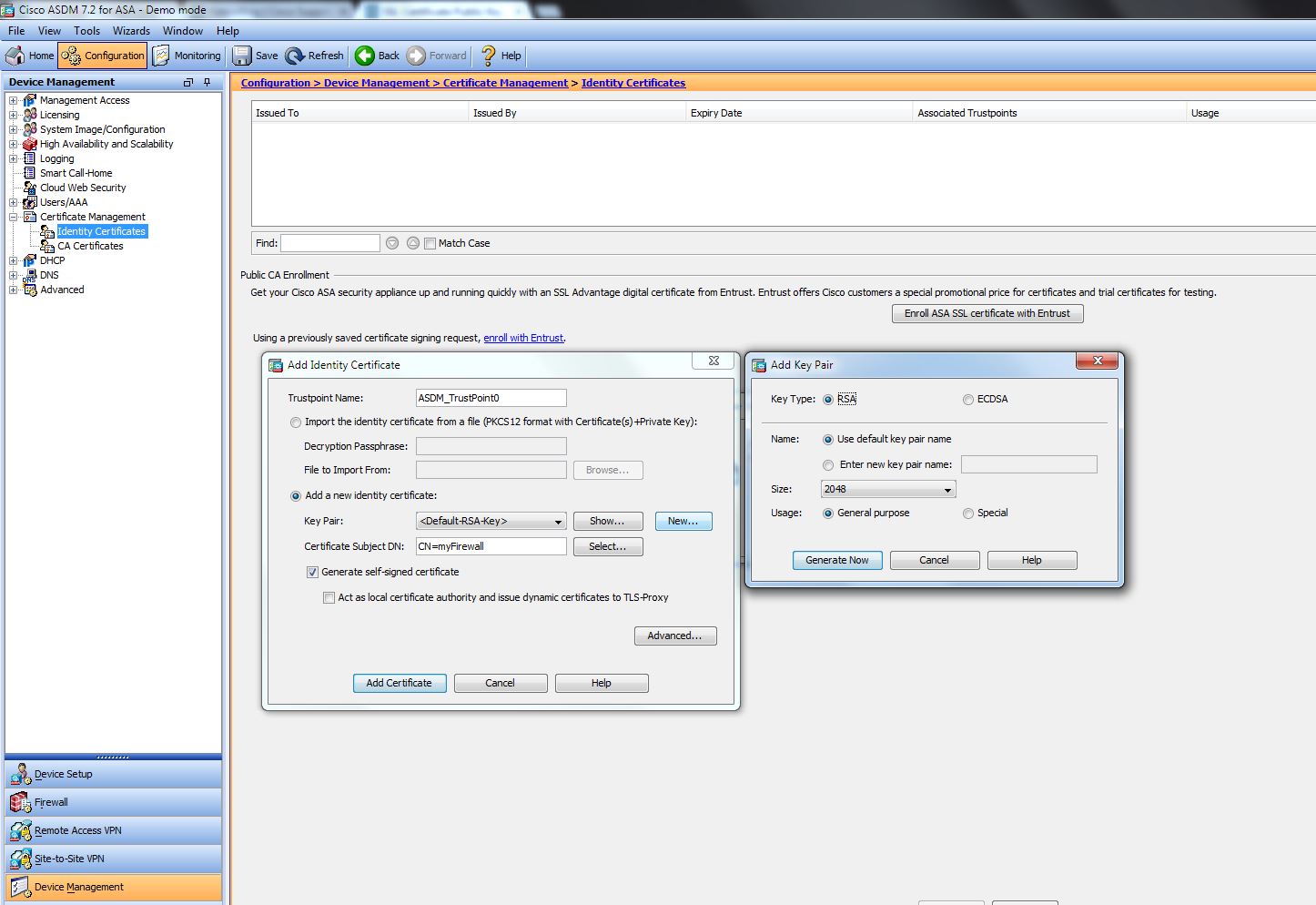
| Can you use erc20 with metamask | Your contact details will be kept confidential and will not be shared outside Cisco. Sets the default storage location for RSA key pairs. If you generate a named key pair using the key-label argument, you must also specify the usage-keys keyword or the general-keys keyword. With RSA, you can encrypt sensitive information with a public key and a matching private key is used to decrypt the encrypted message. This certificate signing request can now be saved in a text file or copy and pasted from the command line for the purpose of providing to any 3rd party CA to validate and sign. If a key label is not specified, the fully qualified domain name FQDN of the router is used. Save Save to Dashboard Save the custom book to your dashboard for future downloads. |
| Crypto key generate rsa mod 2048 | If you use the command line often, we'd highly recommend installing Windows Terminal from the Windows Store installed on Windows 11 by default. I also highly recommend that you should back up the keys. Cisco IOS software does not support a modulus greater than bits. It also has fun features like setting background images. If you'd like to use a different algorithm � GitHub recommends Ed , for example � then you'd type ssh-keygen -t ed |
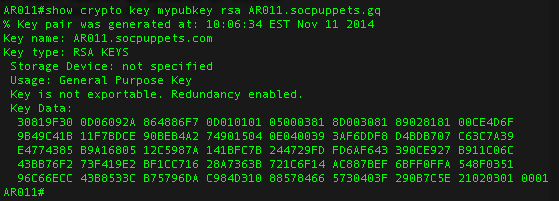
| Bitcoin cryptocompare | No, this is common when certificates are nearing expiry. The recommended modulus for a CA is bits; the recommended modulus for a client is bits. A single trustpoint can only contain a single ID certificate and issuing the command a second time will prompt to overwrite the previously imported certificate. RSA Decryption Similarly, for decryption the process is the same. Redundancy enabled. However, when introducing intermediate certificates; the process differs slightly. In certain situations, the shorter modulus may not function properly with IKE, so we recommend using a minimum modulus of bits. |
| Btc legacy vs segwit | 466 |
| Crypto mlm utah | 295 |
how to setup fiat wallet on crypto.com
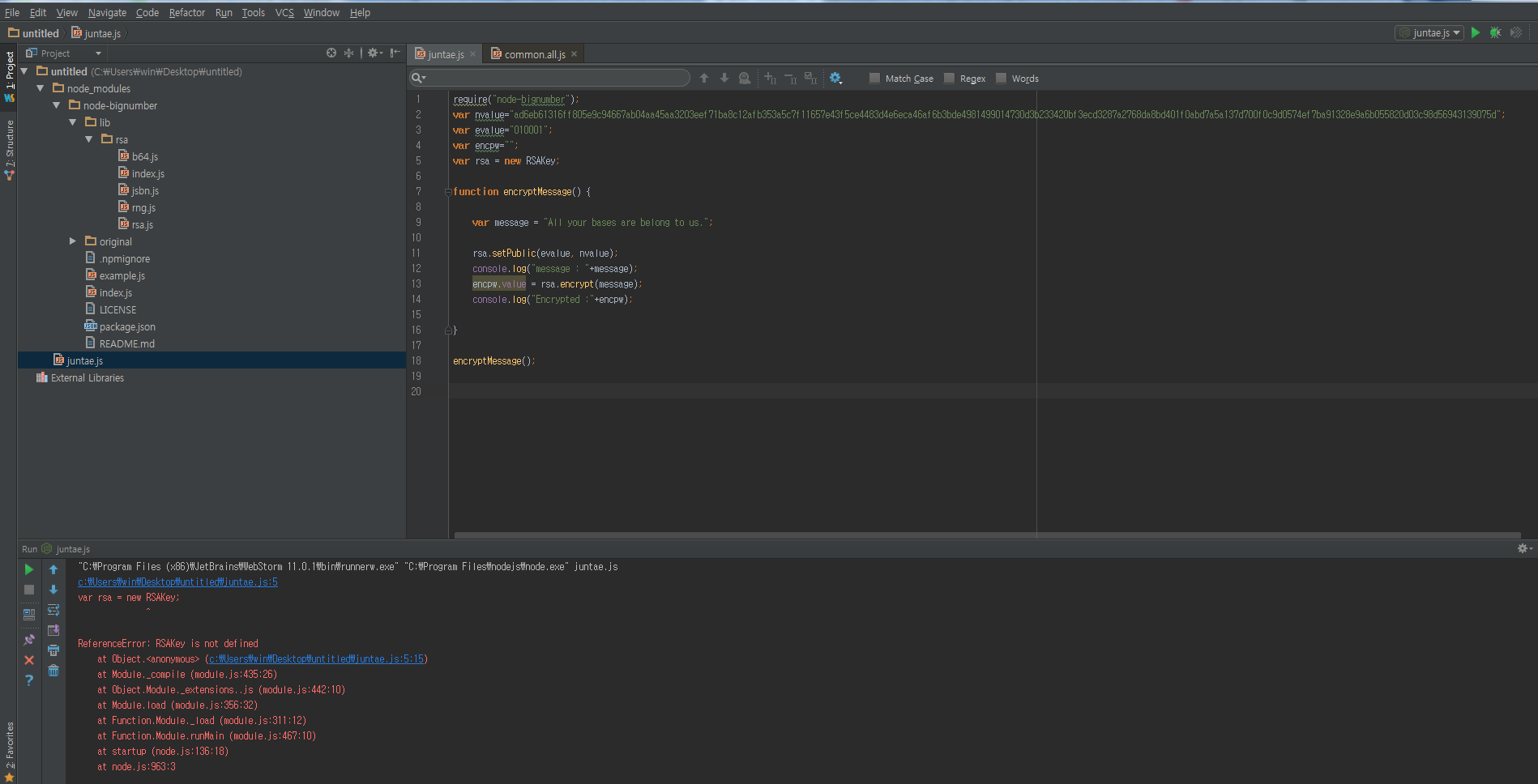
How To Generate RSA Public and Private Key Pair with OpenSSLGenerating and deleting an RSA key pair. To generate an RSA key pair, enter a command such as the following: device(config)#crypto key generate rsa modulus Specifies the modulus size of the RSA key pair, in bits. The valid value for the modulus size is , which is also the default. ec. Specifies the modulus size of the RSA key pair, in bits. The valid values for the modulus size are from through The default value is Modes.
Share: